Disruptive Electronics
Sometime in the near future.
Aircraft carrier USS George Washington in the Taiwan Straits detects an incoming missile. Its electronic signature reads “carrier killer.” Instantly, the U.S. Commander initiates countermeasures. He smacks the button …
Nothing.
In the seconds before the enormous flash, his screen blinks: “Oops, 504! Something did not respond fast enough, that’s all we know … ”
Dismiss this nightmare scenario as forays of the imagination from the likes of Tom Clancy or John le Carré, but for a team of engineers at USC Viterbi’s Information Sciences Institute (ISI), the danger is clear and present.
Integrating expertise in novel electronics, computer networks, cyber security, X-ray tomography, quantum computing and artificial intelligence, these scientists are anxiously aware that with exponential complexity comes exponential threat. They’re creating the first national center that moves beyond viruses and malicious programming in software to the ominously emerging problem of malicious hardware — the SecUre and Robust Electronics (SURE) Center.
In May 2012, the Senate House Armed Services Committee released a report revealing counterfeit electronics were found in U.S. military vehicles, including Navy surveillance aircraft.
If phony chips can infiltrate the Pentagon and possibly destroy a $12 million THAAD (Terminal High Altitude Area Defense) interceptor with a $2 part, what about the electronics that run our lives? Consider your car, a computer on wheels. In July 2015, a pair of hackers demonstrated just how easily they can drive off to any place at any speed, totally against your will.
Software vulnerabilities like this receive plenty of press. The emerging hardware threat is mostly off our radar. Imagine buying a cell phone, printer, screen or any other device in which malicious instructions, kill switches and security backdoors are etched permanently into the silicon you think you control.
These “Hardware Trojans” can be inserted at any phase: production, testing or distribution. They can simply self-activate or be triggered with a click thousands of miles away. Perhaps more unnerving, the United States does not have a comprehensive system to certify that integrated circuits (ICs) do not contain components with a hidden agenda.
“The exodus of microelectronics production is certainly not a new phenomenon,” said Matt French, SURE Center co-director, who oversees the fine-grained computing and wireless networking groups at USC ISI in Arlington, Va.
“It started in the ’80s, when large U.S. integrated circuit chip designers began moving to offshore fabrication facilities (or ‘fabs’) to create economies of scale,” French said. “In this way, they avoided having to shell out the over $2 billion necessary to build a plant. It freed up capital and time for innovators to do what they do best — design newer and better chips.”
Today, almost every new American chip company is “fabless,” allowing the industry to remain vibrant and avoid competitive siege. In all, less than 25 percent of the world’s chipmaking capacity remains in the United States.
 “But the savings come at a hidden cost,” added Draper, SURE Center co-director and leading authority in resilient computing. “The evolving economics of production also spawned a shadow market of counterfeit electronics, and offshoring hasn’t done much to improve quality perceptions, forcing us to ask: ‘What happens now when something that we used to count on being 100 percent correct all the time is only correct 99.9 percent of the time?’”
“But the savings come at a hidden cost,” added Draper, SURE Center co-director and leading authority in resilient computing. “The evolving economics of production also spawned a shadow market of counterfeit electronics, and offshoring hasn’t done much to improve quality perceptions, forcing us to ask: ‘What happens now when something that we used to count on being 100 percent correct all the time is only correct 99.9 percent of the time?’”
Apply the laws of reliability to a supercomputer that manages air-traffic control or a city’s power grid. “[It’s] made up of billions of parts,” Draper said. “If that reliability goes down even one-thousandth of a percent, and we use the multiplicative equation to determine overall system reliability — we lose a lot. This is a major concern in the supercomputer world, but it goes all the way down to handhelds.”
So what is the SURE Center’s solution? First, introduce quality metrics across the industry — the T.S.R.R. of electronics. “Effective hardware needs to be Trustworthy, Secure, Resilient and Reliable,” said French. “You can’t possibly test for an infinite number of functions for chips with hundreds of millions of logic gates, but at minimum you should check the basics.”
French and his ISI colleagues want a method to diagnose circuits in real time, especially for the U.S. Department of Defense and other clients. For this, they turn to Michael Bajura, a lead researcher at ISI who helped design and develop the ultimate chip X-ray machine.
“Casting the chip-imaging problem into a medical imaging problem was a great opportunity,” Bajura said.
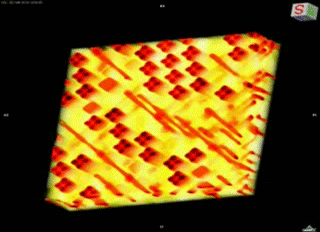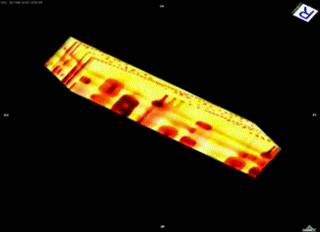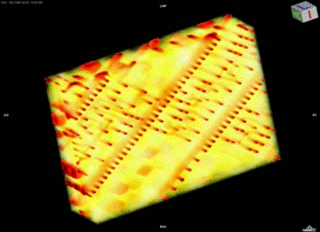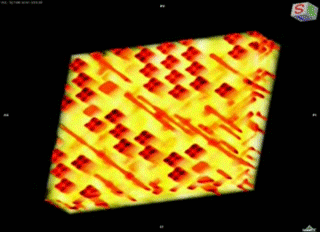
Using a powerful transmission X-ray microscope at Stanford’s Synchrotron Radiation Lightsource, based on an Xradia lab model, Bajura developed nanoscale computerized tomography (CT) methods to obtain nondestructive high-resolution 3-D images of integrated circuits. He then scanned them for defects and modifications. “Because ICs are very large compared to a microscope’s field of view [30 microns], we had to come up with methods that could deliver images of individual chip layers on a scale of automation and accuracy that’s never been done before,” Bajura said.
They’re creating the first national center that moves beyond viruses and malicious programming in software to the ominously emerging problem of malicious hardware.
Formerly, this method involved scanning electron microscopy (SEM), a method much like that of an archaeologist photographing and documenting each layer before scraping it away and moving down to the next. “At the end of the day, you were left with a pile of dust and an expensive chip destroyed,” Bajura said. His new X-ray nanotomography method, however, manages to peer through each layer quickly and sharply without disturbing the chip.
The SURE Center is also focusing on developing anti-tamper methods that can pick up an attack in real time. “Traditionally, anti-tamper required something physical surrounding the device,” Draper said. “We want to create something built-in that senses and tattles on a malicious encounter. Think of it as a microchip’s internal immune system.”
But innovators like Draper and French emphasize that the primary attribute of the SURE Center is not that of the “night watchman,” which attends only to military and security applications. They understand the interlink between a secure defense system that doesn’t play by the rules of international trade and a robust commercial environment that does.
“ISI is a major innovation center for creating prototypes for all users,” French said. “We have the ability to cross-pollinate with experts from various disciplines to produce new technologies in fields like space electronics, and embedded and high-performance computing.”
MOSIS, the decades-old chip brokerage firm under the direction of Wes Hansford, fulfills this critical need. MOSIS divides up the space to manufacture scores of different prototypes, spreading the cost for chip developers while giving academic researchers, and even students, opportunities to realize thousands of new designs.
“If we’re going to convince the electronics world that we need to start doing some of these things more reliably, we have to show lower-cost approaches to adding some of this redundancy,” Hansford said.
He is teaming with French, Draper and Bajura under the SURE Center umbrella to form a community that will develop new processes for collaborative design and change current notions of time-to-market in radical ways.
At USC’s ISI, they stand in the earliest tradition of large-scale integration, having begun with the ARPANET, which was originally created to keep electronic communications alive during and after a nuclear attack.
“A lot of our disruptions in technology sparked from a critical governmental need,” French said. “In time, the innovations cascaded down to everyday consumers and transformed our world.”




